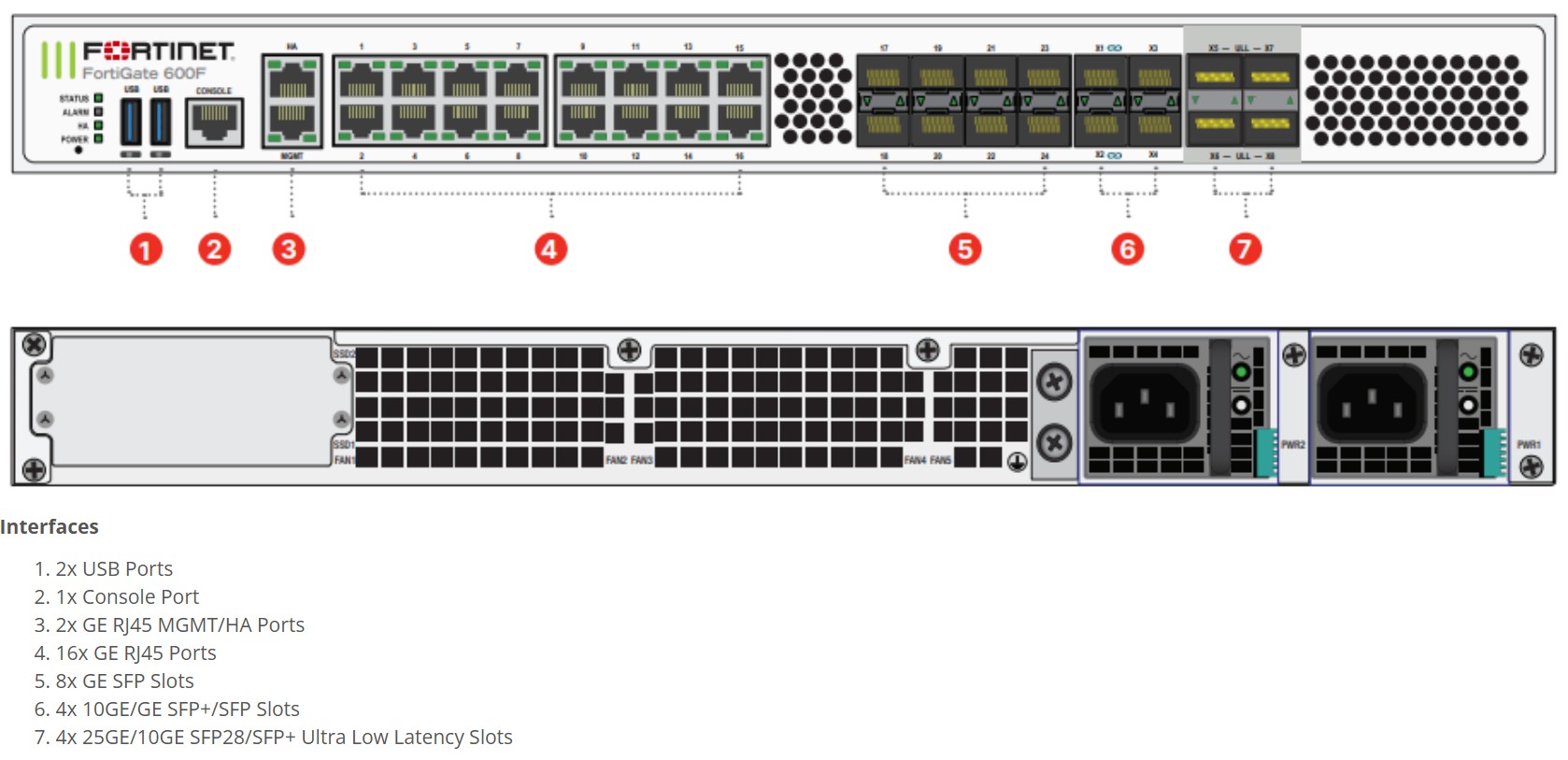
Moving From Palo Alto to a FortiGate 600F: My Experience and Key Takeaways
I recently completed a transition from a Palo Alto firewall to a FortiGate 600F. Both platforms sit at the higher end of the market, and both deliver strong security features, so this was not a decision driven by shortcomings. Instead, it was guided by changes in scale, budget, and operational needs.
What I valued in Palo Alto
Palo Alto has long been recognised for clear application visibility and strong threat detection. The App-ID system makes it straightforward to identify traffic types without relying on port numbers alone. This gives accurate control and clarity when shaping policies.
The interface is also very neat, with a layout that makes policy tracking and log analysis direct and methodical. For teams that manage large policy sets, this level of polish is a welcome advantage.
In addition, the platform offers deep content inspection and tight integration with cloud-based threat intelligence. This helps security teams stay aligned with current attack patterns.
Why FortiGate 600F stood out
The FortiGate 600F brings strong performance for mid-to-large networks. Its security processing units offer high throughput even with deep inspection enabled. This makes it attractive for environments where traffic volumes continue to rise.
FortiOS is also known for being flexible. Administrators can manage routing, SD-WAN, wireless controllers, and VPN from a single system. For organisations that need multiple functions in one device, this blend of roles adds real value.
Another factor is licensing. Fortinet’s licensing model can be more straightforward for long-term planning, which helps when budgeting across multiple years.
The Fortinet ecosystem is wide, with switches, wireless access points, NAC, and logging platforms that integrate neatly. This means a single vendor can support much of the network stack without adding management layers or separate dashboards.
Final thoughts
The move from Palo Alto to a FortiGate 600F has not been about leaving a weak product behind but rather choosing a platform that aligns better with current network size, expected growth, and management style.
Palo Alto gave excellent visibility and strong application control.
FortiGate 600F now brings high throughput, flexible deployment options, and broader ecosystem integration.
Both platforms hold their place in the security market. The decision came down to what fits the environment today and supports where the network is heading.